The last few years have been all about BYOD – or bring your own device – an IT revolution that has freed employees from the shackles of dated or unsuitable hardware in favor of, well, whatever they wanted to use. Allowing access to corporate email and information on their phones, tablets, and even laptops, whether they are iOS, Android, or Windows based. The benefits are obvious: most employees have their own computers at home and know how to use them, so they can spend more time getting down to business and less time trying to work out why this application doesn’t have that feature. This easily leads to increased productivity and reduced costs.
But there are big drawbacks to BYOD as well, and most of them concern security. First there’s the fact that company data is leaving the premises every evening, and what happens to it off-site often has IT staff pulling their hair out. If not fully understood and regulated, BYOD can threaten IT security and put a company's sensitive business systems at risk.
At KIX Consulting we work with your business and provide solutions to keep the security of your data, allowing your business to have a truly mobile workforce.
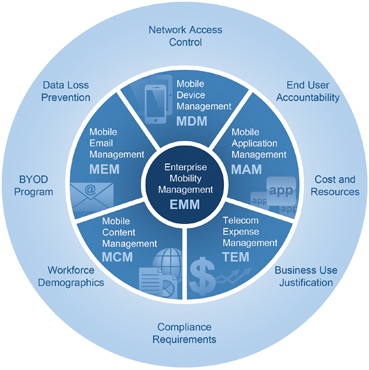
Enterprise Mobility Management (EMM) is an all-encompassing approach to securing and enabling employee use of smartphones and tablets. In addition to addressing security concerns, a strong EMM strategy also helps employees be more productive by providing them with the tools they need to perform work-related tasks on mobile devices.
EMM typically involves some combination of mobile device management (MDM), mobile application management (MAM) and mobile information management (MIM). MDM focuses on locking down mobile devices, while MAM focuses on controlling which users can access which applications and MIM focuses on allowing only approved applications to access corporate data or transmit it.
These three technologies all address specific concerns, but do not provide complete solutions for the problems that enterprise mobility can cause or make worse. The overlap between MDM, MAM and MIM is actually quite minimal. The challenge lies in managing all three concerns with minimal overhead. As more organizations adopt enterprise mobility management, vendors have started to productize EMM, usually by adding MAM or MIM features to their MDM products or vice versa. An Enterprise App Store or other application delivery and deployment technology is also a common component of EMM products.
Contact us via email at inquiries@kixconsulting.com or contact Our Team
|
Please Visit Us Again | Thankyou